FreeLAN VPN

FreeLAN - the multiplatform VPN-client who extends under licence GNU GPL and concerns so-called class Full Mesh, that is uses P2P-technologies. The project concerning young, has actively started to move ahead only since 2013.
Its main difference from other projects is a choice of an architectural option: client server (as habitual VPN, clients depending on installations can or cannot exchange the data with each other, the server can act as relays), P2P (clients are connected to each other directly) and mixed (both variants).
Thus, it is possible to adjust flexibly VPN practically under any conditions. For example, the server can be necessary to get access to an internal network or for control of connections, in other cases it is possible to allow to be connected directly.
As basis own report FSCP (FreeLAN Secure Channel Protocol), based on UDP serves. Can work as at level Ethernet, installing direct Ethernet-connections between sites, and at level IPv4/IPv6. Authorisation by a confidential word and under X.509-certificates, the minimum size of open key RSA - 1024 bits, recommended - 2048 bits is provided, as a symmetric key is used AES-256.
Sessions have the limited service life after which termination are restarted, messages contain counters and supervise time that allows to avoid replay-attacks. For session maintenance messages keep-alive go. The message heading subscribes a private key or HMAC-SHA-256 if the pre-shared-key is used. In general, a choice in options very big.
Are supported Win, Linux, macOS, Raspberry Pi. The package is in repositories of the basic distribution kits, therefore installation of complexities does not cause. Upon the program represents one binary, therefore to create networks very simply.
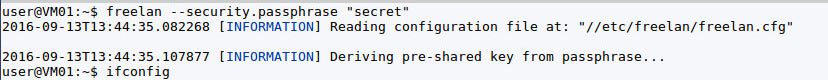
By default the server will open port UDP/12000 on all interfaces, the virtual interface will receive 9.0.0.1 address. Using additional parametres, they can be redefined, as well as to specify certificates. We are connected to the server from other site, we will appropriate to it another internal IP:
For convenience all options can be placed in a configuration file. At installation in Ubuntu already there is a ready template/etc/freelan/freelan.cfg which will be read at start, and therefore it is better to bring in it parametres at once. Alternative FreeLAN - PeerVPN or Cjdns in which also use the distributed technologies.
We lift server FreeLAN
Configuration file FreeLAN
Other VPN programs: