It is enough to spend the cursor over the link in file PowerPoint to catch a malware

Distribution various a malware by means of harmful files Office (more often hackers infect documents Word) is for a long time tactics checked up by malefactors. As a rule, such attacks include an element of social engineering and use macroes VBA in the document.
Independent expert Ruben Daniel Dodge, and also experts of company SentinelOne, warn about occurrence of new technics of attacks which uses files PowerPoint and looks more dangerous than already habitual dodges with macroes.
Researchers inform that harmful files extend through spam letters with subjects of kind RE:Purchase orders #69812 or Fwd:Confirmation. In such messages it is possible to find out investments with names order&prsn.ppsx, order.ppsx and invoice.ppsx. Sometimes files happen are packed in ZIP-archives.
The file of harmful presentation contains only one slide, and he can be seen on an illustration more low. The inscription which also is the link, says: «Loading … Please, wait».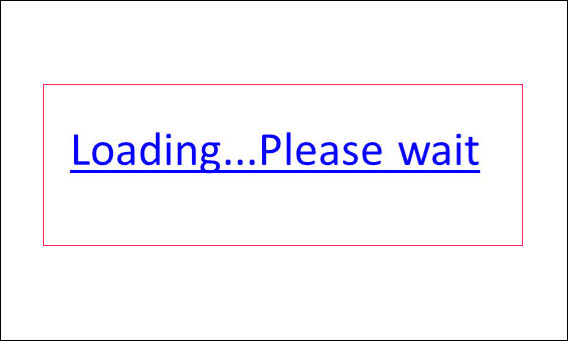
As no loading happens, the user will probably want if not to click the link probably casually to guide at it the cursor, and it will provoke attempt of performance of code PowerShell. If at a victim protective function Protected View, active in the majority of supported versions Office is thus included, the system will warn the user about danger and will stop attack.
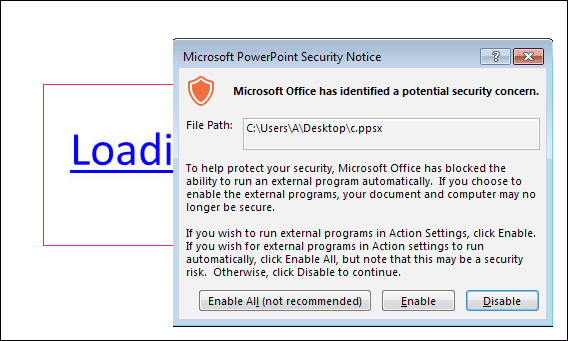
However if Protected View does not work, or the user has decided to neglect the prevention, harmful PowerShell will work that will lead to loading on the file computer c.php from the domain cccn.nl. Experts write that according to their analysis, such method new versions of the bank trojan known under names Zusy, Tinba or Tiny Banker extend.